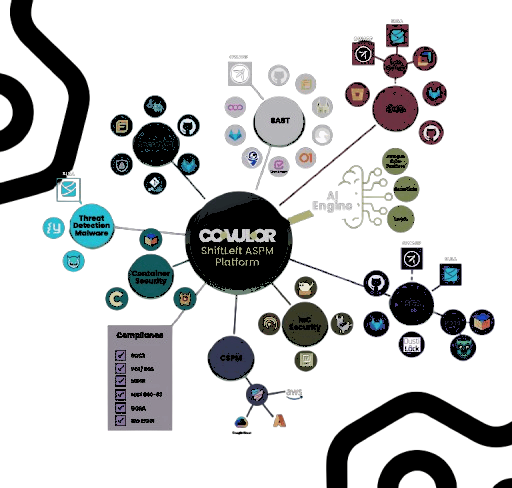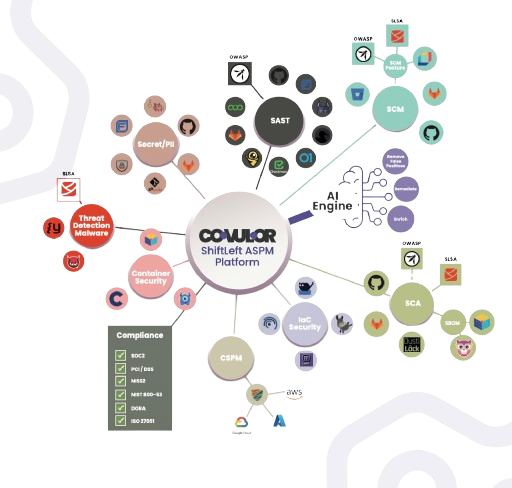
Welcome to Plexicus Documentation
Plexicus is the leading AI-powered Cloud-Native Application Protection Platform (CNAPP), built to secure your entire cloud-native lifecycle from code to cloud. Designed for modern development and cloud environments, Plexicus provides a unified platform to identify, prioritize, and remediate risks across your applications, infrastructure, and workloads with unprecedented efficiency. Our platform automates critical aspects of application security, helping your teams:- Streamline Security Workflows: Automate vulnerability identification, enrichment, and remediation to reduce manual intervention by up to 95%.
- Ensure Compliance: Maintain adherence to industry standards like PCI DSS, SOC 2, NIST 800-53, and more.
- Seamlessly Integrate: Work effortlessly with your existing tools such as GitHub, GitLab, Bitbucket, and other CI/CD platforms.
Workflow
-
Initiating Repository Analysis:
An Admin, Cyberoper, or Developer begins by analyzing a new repository. -
Findings Creation:
Once the repository is analyzed, AI generates findings and suggests improvements. -
File Editing and Review:
- The Admin or Cyberoper reviews and edits the file containing AI-driven improvements.
- They send the edited file to the Developer.
-
Developer Review and Finalization:
- The Developer analyzes the suggested improvements.
- They can make additional edits or finalize the changes by creating a pull request to update the file.
Role Differences
| Action | Admin | Cyberoper | Developer |
|---|---|---|---|
| Add Members to Team | Yes | No | No |
| Analyze Repositories | Yes | No | Yes |
| View All Findings | Yes | Yes | No |
| Send Findings to Dev Team | Yes | Yes | No |
| Edit File | Yes | Yes | Yes |
| Make Pull Request | Yes | No | Yes |
| Request Review | No | No | Yes |